Docker Swarm, Portainer and Traefik combined
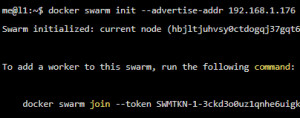
As mentioned several times on this page, I primarily use the reverse proxy Traefik to access my Docker containers. To be able to manage the containers in a graphical GUI, I also use Portainer. For a single server, the setup fits so far, but if you want to deploy multiple servers, you can use Docker-Swarm for that. I first tested Portainer in combination with Swarm and extended the setup with Traefik including SSL with Let's Encrypt.
Portainer and Swarm: Stack Deploy
Who installed Docker and initialized Swarm, you can start Portainer by creating the following configuration:
Contents of file: portainer-agent-stack.yml:
version: '3.2'
services:
agent:
image: portainer/agent:2.14.2
volumes:
- /var/run/docker.sock:/var/run/docker.sock
- /var/lib/docker/volumes:/var/lib/docker/volumes
networks:
- agent_network
deploy:
mode: global
placement:
constraints: [node.platform.os == linux]
portainer:
image: portainer/portainer-ce:2.14.2
command: -H tcp://tasks.agent:9001 --tlsskipverify
ports:
- "9443:9443"
- "9000:9000"
- "8000:8000"
volumes:
- portainer_data:/data
networks:
- agent_network
deploy:
mode: replicated
replicas: 1
placement:
constraints: [node.role == manager]
networks:
agent_network:
driver: overlay
attachable: true
volumes:
portainer_data:When using Docker-Swarm, containers can be created and launched using the "stack deploy" command:
Stack Deploy
me@l1:/var/docker/portainer$ docker stack deploy -c /var/docker/portainer/portainer-agent-stack.yml portainerGUI
The portainer GUI can now be started using the IP address of the server and port 9443 used in the configuration. In my case the server has the IP address 192.168.1.176, so the call is done via https://192.168.1.176:9443/.
For containers to be managed within Portainer, they must be created within it. If you use docker-compose so far, you have to adapt the YML files a bit for Docker-Swarm, see: Docker Compose vs. Docker Swarm: using and understanding..
This stack was created outside of Portainer. Control over this stack is limited.
Portainer can access all Docker resources by mapping docker.sock. Since Portainer itself runs in Docker, Portainer is also listed as a container. Portainer, of course, is difficult to create in Portainer if Portainer has not even been started yet. For this reason, Portainer must remain an exception, and it naturally makes sense that its container can only be managed in a limited way.
The following deployment goes one step further by combining Traefik and Portainer into one deployment, including the Traefik dashboard.
Portainer and Traefik incl. dashboard and https internet access (Let's Encrypt)
As a prerequisite for Let's Encrypt a DNS entry and a public IP address is needed, see secure https connection: Traefik Reverse Proxy + Let's Encrypt. The base of this configuration is from the official documentation: https://docs.portainer.io/advanced/reverse-proxy/traefik.
Additionally, I have activated the Traefik dashboard.
services:
traefik:
image: "traefik:v2.8"
command:
#- "--log.level=DEBUG"
- "--api.dashboard=true"
- "--providers.docker=true"
- "--api.insecure=true"
- "--providers.docker.swarmMode=true"
- "--providers.docker.exposedbydefault=false"
- "--entrypoints.web.address=:80"
deploy:
mode: replicated
replicas: 1
labels:
- "traefik.enable=true"
- "traefik.http.routers.traefik.rule=Host(`traefik.yourdomain.com`)"
- "traefik.http.routers.traefik.service=api@internal"
- "traefik.http.routers.traefik.middlewares=traefik-auth"
- "traefik.http.services.traefik.loadbalancer.server.port=8080"
- "traefik.http.middlewares.traefik-auth.basicauth.users=admin:$$2y$$05$$ool59Dzqut1BSYoZkmnqRuZgLJrrbBvM3jV0BmU09lHsunIWEuAsy"
ports:
- "80:80"
- "443:443"
networks:
- public
volumes:
- "/var/run/docker.sock:/var/run/docker.sock:ro"
agent:
image: portainer/agent:latest
environment:
# REQUIRED: Should be equal to the service name prefixed by "tasks." when
# deployed inside an overlay network
AGENT_CLUSTER_ADDR: tasks.agent
# AGENT_PORT: 9001
# LOG_LEVEL: debug
volumes:
- /var/run/docker.sock:/var/run/docker.sock
- /var/lib/docker/volumes:/var/lib/docker/volumes
networks:
- agent_network
deploy:
mode: global
placement:
constraints: [node.platform.os == linux]
portainer:
image: portainer/portainer-ce:latest
command: -H tcp://tasks.agent:9001 --tlsskipverify
volumes:
- data:/data
networks:
- public
- agent_network
deploy:
mode: replicated
replicas: 1
placement:
constraints: [node.role == manager]
labels:
- "traefik.enable=true"
- "traefik.http.routers.portainer.rule=Host(`portainer.yourdomain.com`)"
- "traefik.http.routers.portainer.entrypoints=web"
- "traefik.http.services.portainer.loadbalancer.server.port=9000"
- "traefik.http.routers.portainer.service=portainer"
- "traefik.docker.network=public"
# Edge
#- "traefik.http.routers.edge.rule=Host(`edge.yourdomain.com`)"
#- "traefik.http.routers.edge.entrypoints=web"
#- "traefik.http.services.edge.loadbalancer.server.port=8000"
#- "traefik.http.routers.edge.service=edge"
networks:
public:
external: true
agent_network:
external: true
volumes:
data:
The value traefik.yourdomain.com must be replaced to the DNS record created before. In order to protect the Traefik dashboard with its own username and password, the parameter "traefik.http.middlewares.traefik-auth.basicauth.users" must be modified accordingly. As described in the article"secure https connection: Traefik Reverse Proxy + Let's Encrypt", the parameter for accessing it can begenerated on Linux with the following command: "echo $(htpasswd -nB admin) | sed -e s/\\$/\\$\$/g".
Conclusion
For those deploying multiple Docker servers, Portainer and Traefik provide the basis for container access and management. However, for sensible operation, a central storage for the volumes is needed, see: Moving web servers with Docker containers, theory and practice. For details on Swarm, see. Docker Compose vs. Docker Swarm: using and understanding.
 ({{pro_count}})
({{pro_count}})
{{percentage}} % positive
 ({{con_count}})
({{con_count}})
