Traefik: Forward traffic to another server
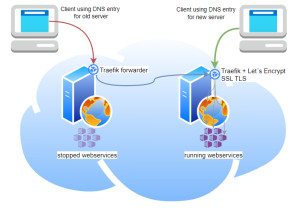
In preparation for moving my websites, I was looking for a way to simply forward all traffic from the old server to the new one.
Change DNS record
Until now, after transferring my websites to a new server, I only changed the DNS entry and waited until it was active everywhere. Within a certain transition phase the accesses landed partly still at the old, partly already at the new server. Of course, the TTL of the DNS entries can be reduced in preparation and thus the transition time minimized, at least for a large part of the accesses, but there is still a certain time in which the version statuses of the servers drift apart somewhat.
To keep the downtime as low as possible during the server change, I simply forwarded the traffic from the old server to the new one this time.
Forward all requests from the old server to the new one.
I copied all Docker volumes: Traefik Reverse Proxy + Let's Encrypt including all websites with rsync to the new server and activated them there. To make sure all access ends up at the destination server, I replaced the Traefik settings at the source server. With the following setup, all accesses can be forwarded to the new server via the IP address of the old server, thus bridging the time until the DNS changes are known across the board:
Traefik docker-compose.yml
version: "3.3"
services:
traefik:
image: "traefik:v2.8"
container_name: "traefikforward2"
ports:
- "80:80"
- "443:443"
volumes:
- "./traefik.yml:/etc/traefik/traefik.yml"Traefik looks in /etc/traefik for a traefik.yml file and tries to load it:
traefik.yml
The following Traefik configuration redirects http and https requests completely to another server. The IP address for redirection here is filled with the placeholder ???.???.???.??? and must be adjusted to match the IP address of the destination server. By using the tls: passthrough option, the complete data traffic is forwarded in encrypted form and thus left to the destination server.
providers:
file:
filename: /etc/traefik/traefik.yml
accessLog: {}
log:
level: DEBUG
entryPoints:
web:
address: ":80"
websecure:
address: ":443"
tcp:
routers:
router4web:
entryPoints:
- web
service: web-forward
rule: "HostSNI(`*`)"
router4websecure:
entryPoints:
- websecure
service: websecure-forward
rule: "HostSNI(`*`)"
tls:
passthrough: true
services:
web-forward:
loadBalancer:
servers:
- address: "???.???.???.???:80"
websecure-forward:
loadBalancer:
servers:
- address: "???.???.???.???:443"
By adjusting the "HostSNI(`*`)" rule of a router, only certain websites could be forwarded (* allows all domain names). Of course, the setup can also be used to specify additional ports, such as 25 when running a mail server. I kept the traefik configuration (traefik.yml) intentionally slim, so that it still remains clear. The content of the traefik.yml file is a simple example and helped me to better understand the individual Traefik modules:
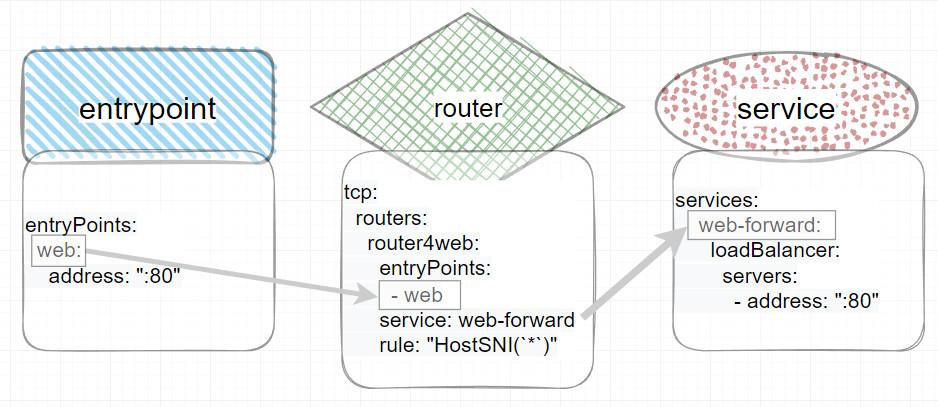
The entryPoints define the accesses, for example to certain ports. An access via an entryPoint can then be processed by a router and passed to a service .
Starting the forwarder
The start is done with the command docker compose up:
docker compose up -dControl accesses
In the traefik.yml file, I set the loglevel to "DEBUG" to be able to observe incoming accesses in the Docker container output. The calls can be easily displayed with "docker logs":
docker logs traefikforward2 -fOutput:
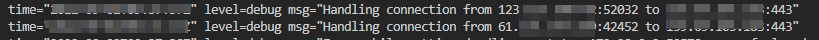
See also, Practical report on moving my web server: move all Docker Websites
For more information on my Traefik setup, see also: secure https connection: Traefik Reverse Proxy + Let's Encrypt.
 ({{pro_count}})
({{pro_count}})
{{percentage}} % positive
 ({{con_count}})
({{con_count}})